Why Are Strings Immutable in Java? Comprehensive Overview for Beginners
Wiki Article
The Evolution of Unalterable String Handling: A Crucial Aspect of Software Application Advancement
In the elaborate world of software program advancement, the handling of immutable strings stands as a cornerstone that has undertaken significant development in time. From its humble origins to the facility challenges run into in early applications, the journey of unalterable string manipulation has been a vital aspect of software engineering. As we browse via the historic landscape of this fundamental principle, mapping the improvements, safety ramifications, and arising fads, we discover ourselves at a juncture where the innate value of understanding this evolution ends up being increasingly obvious.Origins of Immutable Strings
When programmers looked for to improve the integrity and protection of data managing mechanisms,The idea of unalterable strings traces back to the early days of shows languages. Immutable strings describe strings that can not be altered after they are created. This basic concept was introduced to deal with problems relating to data stability and protect against unplanned alterations to critical information saved as strings.
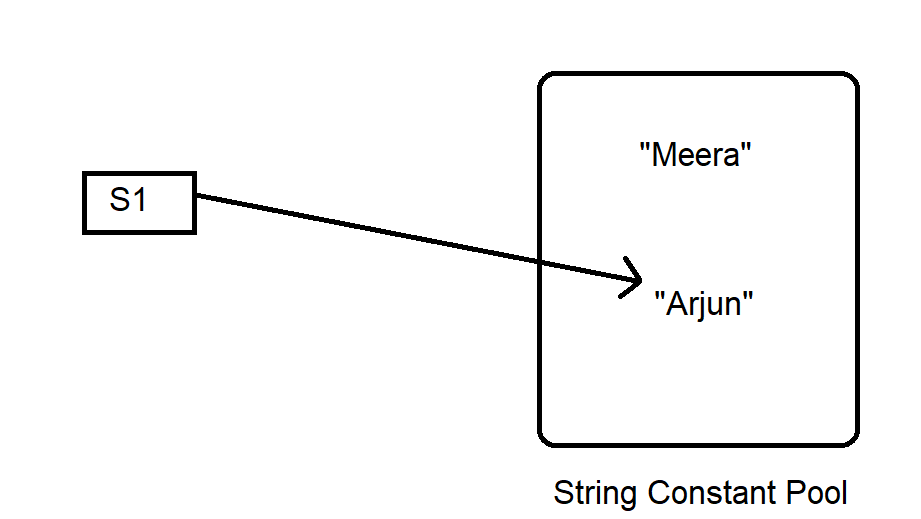
Moreover, immutable strings contribute to improving the general safety and security of software systems (Why are strings immutable in Java?). By preventing unapproved parties from damaging delicate string data, immutable strings help mitigate the threat of data violations and unapproved accessibility to personal information. This fundamental principle proceeds to play a crucial role in modern programming languages and continues to be a cornerstone of protected and durable software program advancement techniques
Very Early Challenges and Solutions
One of the key challenges in taking care of immutable strings was taking care of memory successfully. In addition, making certain that strings stayed unaltered confirmed to be complex, specifically when several parts of the codebase needed to accessibility and change information.To deal with these obstacles, programmers began carrying out information security strategies to shield sensitive info kept in unalterable strings. Security helped guard information from unauthorized accessibility and control. Furthermore, the intro of hashing algorithms gave a way to verify the honesty of unalterable strings by generating one-of-a-kind checksums based upon their contents. If any alterations had occurred, these checksums allowed for quick contrasts to establish. By including security and hashing approaches into the handling of unalterable strings, programmers substantially boosted the safety and reliability of information within software systems.

Advancements in String Immutability
In software program advancement, a notable development in the handling of unalterable strings has emerged with innovations in information file encryption and hashing methods. By utilizing protected hash algorithms like SHA-256 or cryptographic techniques such as AES security, developers can make certain that sensitive info kept in immutable strings i thought about this remains tamper-proof and safe. These developments have bolstered the integrity and discretion of information within applications, especially in markets where data safety is paramount, such as financing, healthcare, and cybersecurity.In addition, developments in string immutability have led the means for boosted performance optimization. Unalterable strings enable much more efficient memory monitoring and caching strategies, decreasing the expenses associated with frequent string controls (Why are strings immutable in Java?). This optimization not just enhances the general responsiveness of software applications yet likewise adds to much better scalability and source utilization
Safety Implications and Ideal Practices
With the structure laid by advancements in string immutability, comprehending the protection ramifications and carrying out best practices comes to be paramount in securing sensitive data within software applications. Unalterable strings play a critical duty in improving security by protecting against unapproved adjustments to data, making sure data integrity throughout the application's lifecycle. By making use of immutable strings, developers can minimize usual vulnerabilities such as injection strikes, buffer overflows, and data meddling, which are usually made use of by harmful actors to compromise systems.This includes encrypting information at rest and in transportation, applying correct accessibility controls, utilizing safe coding techniques, and regularly updating software parts to spot well-known vulnerabilities. By incorporating these protection procedures basics and finest techniques into software program growth processes, companies can better shield their data properties and decrease the risk of safety and security violations and data leaks.
Future Trends in String Handling
Among the ever-evolving landscape of software application advancement, the trajectory of string handling is positioned to witness substantial innovations and innovations. Among the crucial future patterns in string handling is the boosting concentrate on performance optimization. As software applications proceed to expand in intricacy and range, the efficient handling of strings ends up being critical for maintaining optimum efficiency. Developers are exploring new formulas and data frameworks to boost the rate and efficiency of string procedures.Moreover, one more fad coming up is the combination of expert system (AI) and artificial intelligence (ML) in string managing tasks. AI-powered devices are being established to automate and improve numerous string adjustment processes, leading to enhanced performance and accuracy in software advancement process.
Additionally, there is a growing focus on enhancing the safety and security elements of string managing with progressed file encryption methods and safe coding methods. As cyber risks proceed to progress, ensuring the stability and confidentiality of information within strings is coming to be a leading priority for designers. By embracing durable safety procedures, such as file encryption at remainder and in transit, programmers can minimize the risks connected with string adjustment vulnerabilities.
Final Thought
Finally, the development of unalterable string handling has been a vital aspect of software growth, beginning from its beginnings to the advancements made in the last few years. Early challenges have actually been addressed with cutting-edge services, resulting in better safety practices in handling strings. It is necessary for developers to stay upgraded on the most recent patterns in string immutability to make certain the toughness and security of their software applications.Unalterable strings refer to strings that can not be transformed after they are created. Why are strings immutable in Java?. By protecting against unapproved events from meddling with delicate string information, immutable strings company website help mitigate the threat of information violations and unauthorized accessibility to private information. By integrating encryption and hashing techniques right into the handling of unalterable strings, developers considerably enhanced the protection and reliability of data within software systems
Immutable strings permit for much more effective memory monitoring and caching methods, lowering the overhead linked with regular string adjustments. Unalterable strings play an important role in improving safety by preventing unauthorized modifications to information, making sure data honesty throughout the application's lifecycle.
Report this wiki page